Meltdown and Spectre CPU Vulnerabilities and its Remediation
Researchers from Google and the research community have independently discovered one hardware vulnerability each, that focus on a flaw in the CPU. If this flaw is taken advantage of, it can enable a hacker to get access to data from the privileged kernel memory.
The two security flaws are named as Meltdown and Spectre and both of them are deemed to be serious flaws, and makes the situation worse is that they are pretty commonly found within CPUs. This vulnerability is considered an important flaw for critical datacenter and cloud deployments and must be addressed to prevent potential future impact. This may include running content from webpages loaded in web browsers or accessed through apps.
Since this flaw impacts almost all microprocessors, it can affect any device that uses them, including multiple operating systems running on mobile devices, laptops, workstations and servers. However, it is of utmost importance to note that an attacker would be able to exploit this vulnerability only if he manages to execute malicious or suspicious code on the target physical system or on a virtual system that is linked to it. This may include running content from webpages loaded in web browsers or accessed through apps.
Know about Meltdown and Spectre
Meltdown is a flaw that attacks and destroys the hardware barrier that exists between the applications that are accessed by users and the highly protected core memory of the device. This is threatening because the the security flaw essentially melts security boundaries enforced by the hardware.
Spectre, on the other hand, functions a little differently as it makes it possible attackers and hackers to trick bug-free applications into revealing highly confidential information. Haunting as it sounds, the name is based on the root cause that is speculative execution.
The Devices that are Affected?
What makes Spectre really dangerous is the fact that it can affect just every computing device, which includes desktops, laptops, tablets, smartphones and even the cloud computing systems. However, some lower power devices are safe at the moment, and this includes certain Internet of Things (IoT) gadgets.
The Cause of Concern
So, what makes it a cause of immediate concern? It’s simply the fact that Meltdown targets the kernel – the core system which is the storehouse of highly sensitive information in the system memory. This can have far-reaching consequences as it would mean everything from highly sensitive banking and credit card information, financial data, and account credentials to a lot more of highly confidential information is at risk.
The fact that Spectre can trick applications to reveal confidential and sensitive data implies that literally every bit of information available on the apps is prone to data theft, and this includes login credentials and other information.
The Important Instructions:
Users have little options other than to act fast and update their systems with the latest security updates at the earliest. The good news is that the fixes for Linux and Windows operating systems are already available. Chromebooks need to upgrade to Chrome OS 63.
Android devices, Google’s Nexus and Pixel smartphone, that run the latest security updates, are already protected. Third party smartphone manufacturers of Android devices, such as Samsung and OnePlus, are expected to roll out updates soon to tackle the threat. For users of Apple’s devices, the company has already published a blog post to inform users to update their devices’ operating system and only download software from “trusted sources such as the App Store”. They also added that “there are no known exploits impacting customers at this time”.
Now since it calls for the attacker to place a malicious code into the system or on a virtual machine attached to it, in order to exploit the vulnerability, the trick lies in preventing unauthorized access from external users and also implement access control for users within the infrastructure.
Hence the bottom line is to implement some of the key security steps immediately.
- Prevent execution of unauthorized software
- Prevent access of untrusted websites
- Apply regular patch updates to system firmware and OS
- Ensure strict adherence to security policies
How to check my PC is protected?
To check if the required patch has been successfully installed, follow the path given below.
Settings > Update & security > View installed update history
Windows Patches Installation Guidelines:
Windows 10
- Don’t disconnect, unplug, or turn off your PC during installation.
- Select the Start button, and follow the path: Settings > Update & security > Windows Update,
- Enable ‘Check Online for updates from Microsoft’ update if your system is registered to your organization domain.
- Click on ‘Check for Updates’. This way you’ll have all the windows patches from Microsoft site downloaded and installed on your system.
Windows 8 and 8.1
- Ensure your system is plugged in and connected to the Internet using a non-metered connection. Don’t disconnect, unplug, or turn off your system during the installation process.
- Swipe inwards from the right edge of the screen, tap on Settings, and then tap on Change PC settings. (When you use a mouse, point to the lower-right corner of the screen, move the mouse pointer up, click on Settings, and then on Change PC settings.)
- Click on Update and Recovery, and then tap or click on Windows Update.
- Enable ‘Check Online for Updates from Microsoft’ update in case your system is registered to your organization domain.
- Click on ‘Check for Updates’. This way you’ll have all the windows patches from Microsoft site downloaded and installed on your system
Windows 7
- Click on Start, then type the update in the search box, and in the list of results, click on Windows Update.
- Click on the ‘Check Online Updates’ in case your system is registered to the domain. Else click on ‘Check for Update’.
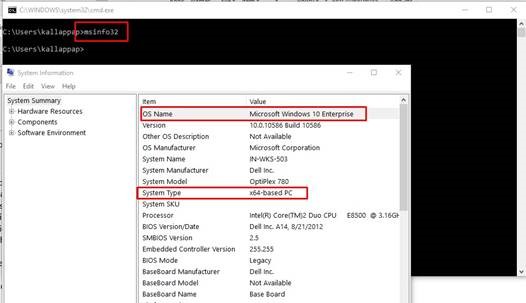
Alternatively, users who are not able to get the security patch from Microsoft online, check your OS and system type using the command below.
MSinfo32
Download patches from below Links and install
Windows 7
32 bit
64 bit
Windows 8.1
32 bit
64 bit
Windows 10
Check your Windows 10 version number using below command in command prompt
Winver

For all editions of Windows 10 with Version 1511
32 bit
64 bit
All editions of Windows 10 with Version 1607
32 bit
64 bit
All editions of Windows 10 with Version 1703
32 bit
64 bit
All editions of Windows 10 with Version 1709
32 bit
64 bit
Windows server 2008
32 bit
64 bit
Windows server 2008 R2
Windows Server 2012
Windows Server 2012 R2
Windows server 2016
Linux Based Systems patches:
Ubuntu 17.10 (Artful) — Linux 4.13 HWE
Ubuntu 16.04 LTS (Xenial) — Linux 4.4 (and 4.4 HWE)
Ubuntu 14.04 LTS (Trusty) — Linux 3.13
Ubuntu 12.04 ESM** (Precise) — Linux 3.2
CentOS version kernel-2.6.32-696.18.7 onwards
